
Gold in the Emerge-Tech Category!
24/08/2021In January 2017, Google released a new feature as part of Chrome version 56 to help users browse more safely online. Here is how the feature appeared, before and after this release. Historically, Chrome did not explicitly label HTTP connections as ‘non-secure’, but this all changed with the version 56 release. Essentially, if a website only had a HTTP connection it was labelled ‘not secure’; if it had a HTTPS connection, it was labelled ‘secure.’
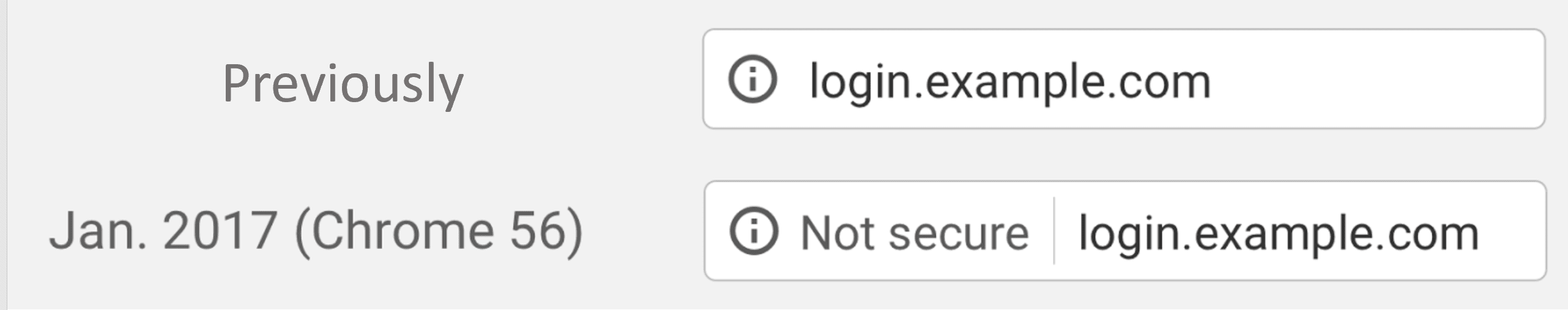
This new feature led to a big change in how people browse the Internet. The impact on user behaviour has been staggering, with a reported 25% drop in user visits to HTTP pages with password or credit card forms on desktop. This drove many of enterprise, eCommerce websites around the world, e.g. asos.com, to update all of their website pages to be HTTPS compliant.
Two years on, Google Chrome 72 deprecates support for TLS 1.0, TLS 1.1 due to the low adoption of valid certificates. We carried out some analysis on this on UK websites, and uncovered thousands that are using a false certificate or none at all!
In a nutshell, this means the end of HTTP-based Public Key Pinning (HPKP), a practice that pins one or more of a website’s public keys in a HTTP header. Ironically it was this practice that would help to defend against mis-issuance of certificates, but in reality it was found by Google and other companies to be potentially dangerous.
HPKP is challenging to use correctly because it’s so difficult to build a set of pinned keys that’s guaranteed to work. This comes as a result of the ever-evolving nature of the digital certificate industry and the variance in user trust stores. As a result, HPKP can cause websites to break and create lots of errors. It can also be weaponized (though there has never been a confirmed case of this happening). Google has already announced its plans to deprecate HPKP, and now support has been removed entirely from Chrome 72.
According to Chris Palmer, Security Engineer at Google, PKP offers a way to defend against certificate mis-issued, by providing a Web-exposed mechanism (HPKP) for sites to limit the set of certificate authorities (CAs) that can issue for their domain. However, this exposes as part of the Open Web Platform considerations that are external to it: specifically, the choice and selection of CAs is a product-level security decision made by browsers or by OS vendors, and the choice and use of sub-CAs, cross-signing, and other aspects of the PKI hierarchy are made independently by CAs.
As a consequence, site operators face difficulties selecting a reliable set of keys to pin to, and adoption of PKP has remained low. When site operators’ expectations don’t match the reality of trust anchors on real world client machines, users suffer. Unexpected or spurious pinning errors can result in error fatigue rather than user safety.
Misuse of Certificates
TAMI analysed 968,659 active websites in the UK. Similar to Google, we found a big problem with over 254,000 sites using an invalid certificate, and 150,000 sharing the same certificates. Why is this significant? Each certificate should be unique to the website or parent company. Let’s look at ASOS:
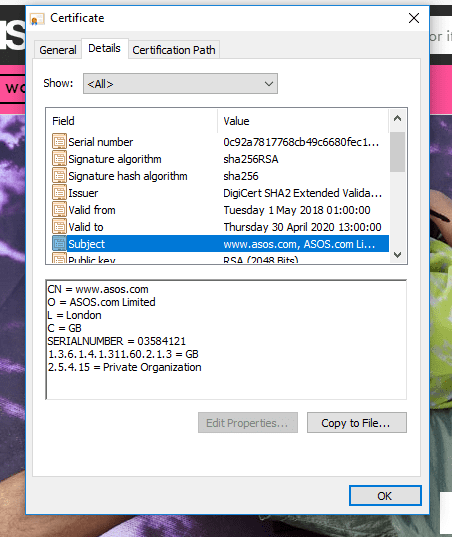
We can clearly see that this certificate is owned by ASOS.com Limited, and the company number is even quoted. Now let’s look at World Food Aid:
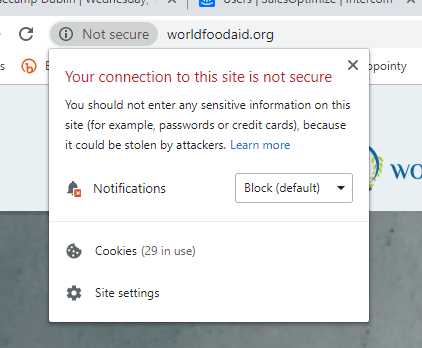
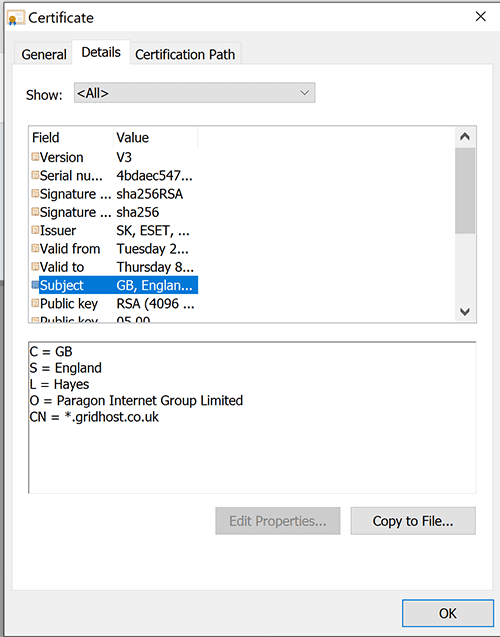
Google has marked this website “Not Secure.” The reason for this is that the company information is incorrect. From our analysis, only 6% of websites that have a valid certificate actually declare their company legal name as well as the website domain name.
Top 10 UK Vendors
Following a review of 968,659 websites, here are the top 10 UK vendors that issue certificates (ranked by number of hosts).
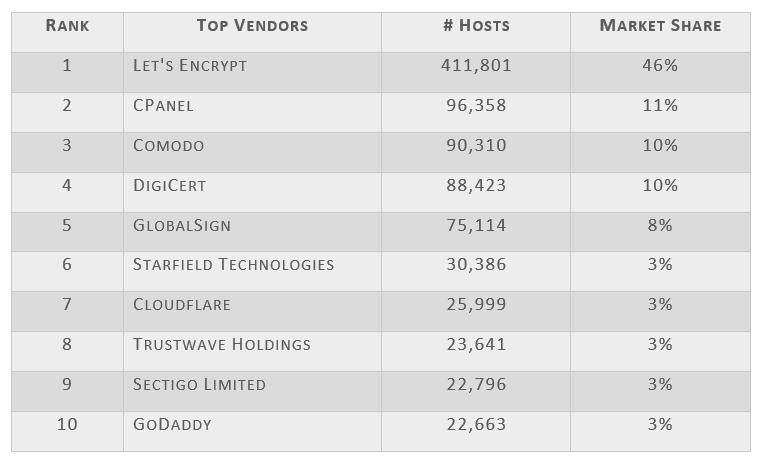
This is the most popular SSL/TLS certificate provider as it scored well with over 93% of sites using valid certificates. Let’s Encrypt is a free, automated, and open certificate authority by the non-profit Internet Security Research Group. Market share: 46%.

cPanel scored well with 93% of sites using valid certificates that are hosted on this platform. cPanel is an online Linux-based web hosting control panel that provides a graphical interface (GUI) and automation tools designed to simplify the process of hosting a website to the website owner or “end user”. Market share: 11%.

74% of websites were found to have valid certificates however we found a high volume using the same certificate. Market share: 10%.

58% of websites were found to have valid certificates however 42% of certificates were invalid. Market share: 10%.

GlobalSign is one of the worst in class when it comes to TLS/SSL certificates, with only 9% of sites having valid certificates. Over 91% of websites were deemed invalid. Market share: 8%.

Only 61% of sites using Starfield Technologies were valid, with over 39% of sites deemed invalid. Market share: 3%.

Although this is not one of the most popular certificate providers, it was the best in class with over 99% of all certificates issued being fully compliant on both website verification and encryption. Market share: 3%.

TrustWave ranked worst in class as a certificate provider, with only 3% of sites having valid certificates. Over 97% of sites performed poorly, as the certificates were invalid. Market share: 3%.

90% of websites had a valid certificate with Sectigo, and only 10% had invalid certificates. Comodo is now part of Sectigo, that claims to be the largest commercial Certificate Authority in the world (however, in the UK they are outranked by Let’s Encrypt). Market share: 3%.

76% of websites using GoDaddy had a valid certificate, with 24% having invalid certs. Market share: 3%.









